
In our initial blog post around the topic, we brought you initial discoveries around Meltdown & Spectre and what ConnectWise was doing in response to the vulnerabilities. Meltdown and Spectre still continue to dominate the security news and the more we delve into it, we are starting to understand the depth and breadth of what this now means for the future of the security landscape.
Turns out the three variants of side-channel attacks, Meltdown and two different for Spectre, were discovered back in June of last year by researchers using speculative execution, which is where processors execute on code and then fetch and store the speculative results in cache. It’s a technique used to optimize and improve the performance of a device. What is important to note with Spectre is that it puts users at risk for information disclosure by exposing the weakness in the architecture of most processors in the market, and the breadth is vast: Intel, AMD, ARM, IBM (Power, Mainframe Z series) and Fujitsu/Oracle SPARC implementations across PCs, physical and virtual servers, smartphones, tablets, networking equipment and possibly IoT devices.
Currently there are no reported exploits in the wild.
Of the two, Meltdown is the easier one to mitigate with operating system updates. AMD processors are not affected by Meltdown. Spectre is a bit more complex to resolve because it is a new class of attack. The two variants of Spectre both can potentially do harm like stealing logins and other user data residing on the affected device. Intel, ARM, and AMD processors are affected by Spectre. Recently, Microsoft released another emergency update to disable Intel’s microcode fix. This original update was meant to patch for variant 2 of Spectre. Unfortunately, that update had adverse effects as there were numerous reports of reboots and instability, so Microsoft issued an out of band update to disable.
Things are still evolving around Spectre and while operating system updates and browser updates are helping to patch for Spectre, it is being reported by some sources that a true fix may be an update to the hardware (processor) itself.
The following is a chart* to clarify each vulnerability:
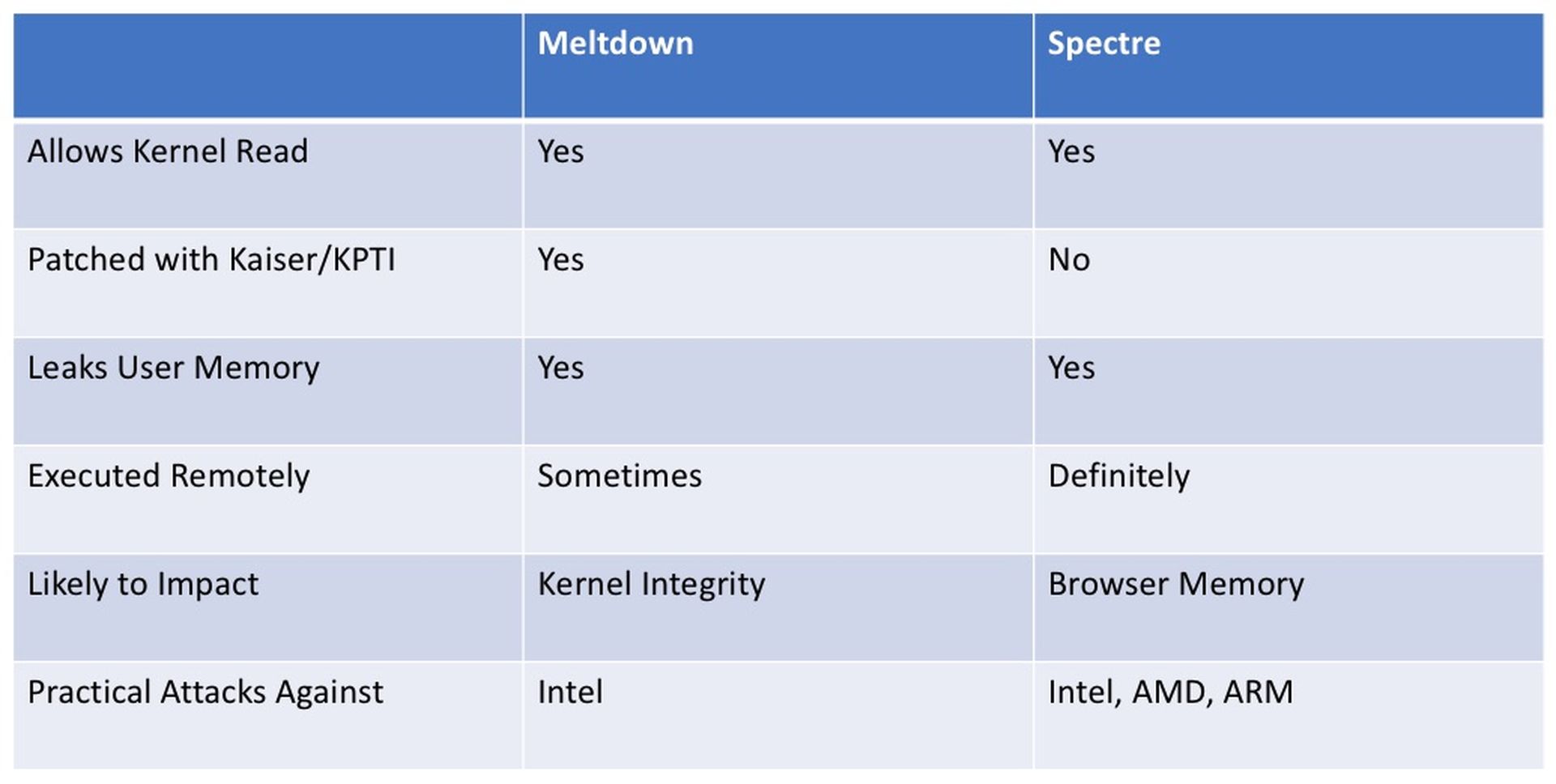
*Chart is courtesy of SANS/Rendition Infosec. See full presentation here.
It will be important over the next few weeks to stay on top of any breaking news around Meltdown and Spectre. Mitigation efforts should be underway in your IT organization to prevent a future zero-day attack.
ConnectWise has your back! Currently we are compiling research and watching closely the progression of Spectre variants to determine the best solution to identify and detect so that we may provide our partners the ability to make an informed decision.
If you are using ConnectWise Automate, check out the Meltdown Dataview we released via the Solution Center a couple weeks ago to help detect agents vulnerable to Meltdown and ensure they have the proper Microsoft released updates using Automate’s Patch Manager.
Brett Cheloff is general manager for ConnectWise Automate. Read more ConnectWise blogs here.




